What Information Is Exposed When You Upload a File?
Data disclosure vulnerabilities
In this department, we'll explain the nuts of information disclosure vulnerabilities and describe how yous can find and exploit them. We'll besides offering some guidance on how you lot can prevent information disclosure vulnerabilities in your own websites.
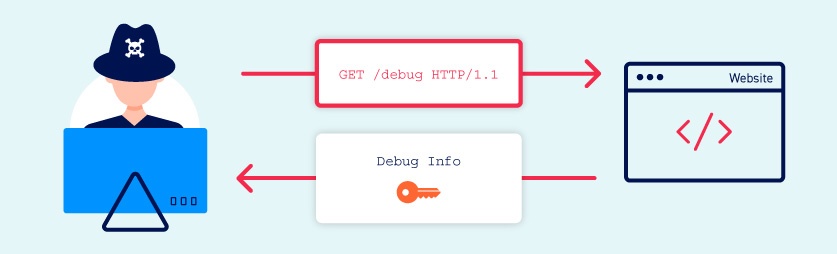
Learning to observe and exploit information disclosure is a vital skill for any tester. You are likely to meet it on a regular basis and, once you know how to exploit it effectively, it can aid you to amend your testing efficiency and enable you to notice additional, high-severity bugs.
Labs
If you're already familiar with the basic concepts behind information disclosure vulnerabilities and just want to exercise exploiting them on some realistic, deliberately vulnerable targets, you can access all of the labs in this topic from the link below.
View all information disclosure labs
What is information disclosure?
Information disclosure, too known as information leakage, is when a website unintentionally reveals sensitive data to its users. Depending on the context, websites may leak all kinds of data to a potential aggressor, including:
- Data most other users, such as usernames or fiscal information
- Sensitive commercial or business data
- Technical details about the website and its infrastructure
The dangers of leaking sensitive user or business data are adequately obvious, simply disclosing technical information tin can sometimes be just equally serious. Although some of this information will be of limited use, it can potentially be a starting indicate for exposing an boosted attack surface, which may contain other interesting vulnerabilities. The noesis that yous are able to gather could even provide the missing piece of the puzzle when trying to construct complex, high-severity attacks.
Occasionally, sensitive information might be carelessly leaked to users who are simply browsing the website in a normal way. More ordinarily, yet, an aggressor needs to arm-twist the data disclosure by interacting with the website in unexpected or malicious means. They will and so carefully report the website's responses to endeavor and identify interesting behavior.
What are some examples of information disclosure?
Some basic examples of data disclosure are equally follows:
- Revealing the names of hidden directories, their structure, and their contents via a
robots.txtfile or directory listing - Providing access to source lawmaking files via temporary backups
- Explicitly mentioning database tabular array or column names in mistake messages
- Unnecessarily exposing highly sensitive information, such equally credit bill of fare details
- Hard-coding API keys, IP addresses, database credentials, and and then on in the source code
- Hinting at the existence or absence of resources, usernames, and then on via subtle differences in awarding behavior
In this topic, you will acquire how to detect and exploit some of these examples and more.
How do information disclosure vulnerabilities ascend?
Information disclosure vulnerabilities can arise in countless dissimilar ways, only these can broadly be categorized as follows:
- Failure to remove internal content from public content. For example, programmer comments in markup are sometimes visible to users in the production environment.
- Insecure configuration of the website and related technologies. For example, failing to disable debugging and diagnostic features tin sometimes provide attackers with useful tools to assist them obtain sensitive information. Default configurations can also go out websites vulnerable, for example, past displaying overly verbose error letters.
- Flawed design and behavior of the application. For example, if a website returns singled-out responses when different mistake states occur, this can besides allow attackers to enumerate sensitive data, such as valid user credentials.
What is the impact of information disclosure vulnerabilities?
Information disclosure vulnerabilities can have both a direct and indirect touch depending on the purpose of the website and, therefore, what information an assailant is able to obtain. In some cases, the human action of disclosing sensitive information alone can take a loftier impact on the afflicted parties. For example, an online store leaking its customers' credit carte du jour details is likely to take astringent consequences.
On the other manus, leaking technical data, such as the directory structure or which 3rd-party frameworks are existence used, may have little to no straight impact. Notwithstanding, in the incorrect hands, this could be the key data required to construct whatever number of other exploits. The severity in this instance depends on what the attacker is able to do with this data.
How to appraise the severity of information disclosure vulnerabilities
Although the ultimate bear on can potentially be very severe, it is just in specific circumstances that information disclosure is a high-severity issue on its ain. During testing, the disclosure of technical information in particular is oft but of interest if you lot are able to demonstrate how an assaulter could practice something harmful with it.
For example, the knowledge that a website is using a particular framework version is of limited utilize if that version is fully patched. Nevertheless, this information becomes significant when the website is using an old version that contains a known vulnerability. In this case, performing a devastating attack could exist every bit simple as applying a publicly documented exploit.
It is important to exercise common sense when you find that potentially sensitive information is existence leaked. It is likely that minor technical details can be discovered in numerous means on many of the websites you test. Therefore, your chief focus should be on the impact and exploitability of the leaked information, not but the presence of data disclosure as a standalone result. The obvious exception to this is when the leaked data is so sensitive that it warrants attention in its ain correct.
Exploiting information disclosure
We've put together some more applied communication to help you identify and exploit these kinds of vulnerabilities. You tin also do these techniques using our interactive labs.
How to prevent information disclosure vulnerabilities
Preventing information disclosure completely is catchy due to the huge variety of ways in which it can occur. However, there are some general all-time practices that you can follow to minimize the risk of these kinds of vulnerability creeping into your own websites.
- Brand sure that everyone involved in producing the website is fully aware of what data is considered sensitive. Sometimes seemingly harmless information can be much more than useful to an aggressor than people realize. Highlighting these dangers can help brand certain that sensitive data is handled more than deeply in general past your arrangement.
- Audit any code for potential information disclosure as role of your QA or build processes. It should be relatively easy to automate some of the associated tasks, such equally stripping programmer comments.
- Employ generic mistake messages as much equally possible. Don't provide attackers with clues about application behavior unnecessarily.
- Double-check that any debugging or diagnostic features are disabled in the production environment.
- Brand certain yous fully understand the configuration settings, and security implications, of any tertiary-political party engineering science that you implement. Have the time to investigate and disable any features and settings that you don't really demand.
Source: https://portswigger.net/web-security/information-disclosure
0 Response to "What Information Is Exposed When You Upload a File?"
Post a Comment